Grenox Sqli Exploit Scanner Serial Key Keygen 56a4c31ff9 460dd52e3b2a041dfa855924eb8a81798b50ab97 1.17 MiB. Havij v1.16 Pro Portable - is an automated SQL Injection tool that helps penetration testers to find and exploit SQL Injection vulnerabilities on a web page. Google Extensa Scanner Version: V3.0.0.1 Added: +New Injection types +Fixed Random crashes +Recode SQLI area +Faster then ever.
The OWASP ZAP tool was created to help users automatically detect security vulnerabilities in web applications while developing and testing them.
The tool can do an SQL injection test by inserting special characters (eg. ', ', 2*3) in all input fields of the target application and monitoring the web page's behavior. If databases errors are discovered on the website, this could be the scenario of an SQL injection attack.
In order to validate the vulnerability found, the SQL Injection scanner attempts to construct a syntactically correct SQL query that demonstrates the injection was successful. That is why the following results will be displayed:
http://vulnapp.example.com/bookings.php?cat=4 AND 1=1 -- The SQL Injection scanner does not attempt to exploit SQL injection, it simply detects the presence of any vulnerability that could affect your backend database. If flaws are detected, our online tool offers detailed information about the risks you are exposed to and recommendations on how to perform an effective remediation process. Start scanning for web applications vulnerabilities today so you will not be exposed to SQL injection attack which let hackers get to tamper with sensitive information (such as usernames, passwords, and other essential credentials) by disclosing, or deleting it.
For more in-depth information about SQL Injection attack, including solutions on how to remediate this vulnerability, you can found on the OWASP SQL Injection Page.
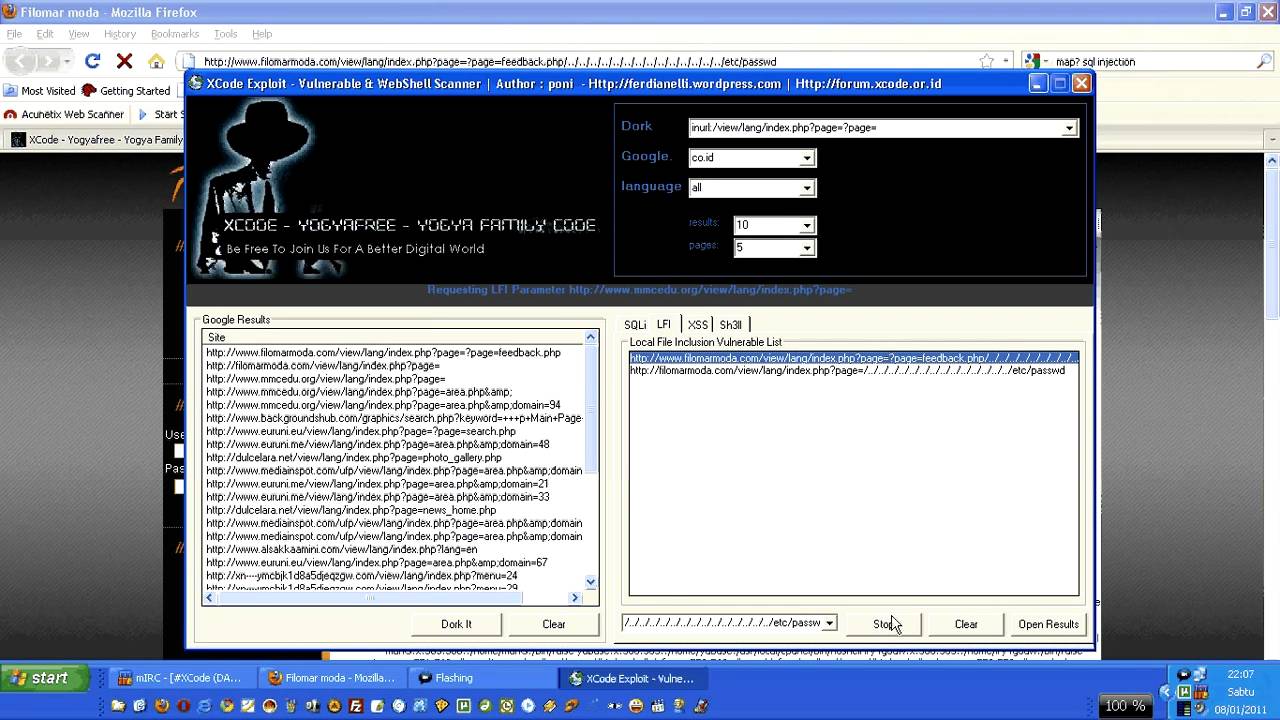
I am PATTAKHA MUNDA From GANGSTER GANG Team .Let me introduce you to Gr3enOx Exploit Scanner ( Most of us might already be using it Big Grin ). Gr3nOx Scans for Vulnerabilities in websites using Google Dorks. So all You have to do is give it some dorks and it'll fetch you some Vulnerable websites! I primarily use it for find websites having SQLI vulnerebility, but you can try LFI, RFI and even XSS!
I am also sharing 8500 SQLI Dorks, find the links below!
Justice v Crookers n Busy P - Protect and Stress (Jeel Mash).mp3SUV (Armand Van Helden Remix).mp3Hip Hop Changed (Busy P Remix).mp375 Mixed Live by Zdar of Cassius.mp3Stress (Auto Remix).mp3Love.mp3Look Better When I'm Drunk.mp3- The Sounds Of Silence (1966).zipGraduate Soundtrack.zipWhite Tie Affair Better When I'm Drunk (Strobonic Electro Mix) www.freshnewtracks.com.mp3White Tie Affair - Better When I'm Drunk (Strobonic Electro Mix) www.freshnewtracks.com.mp303. 
There are also six denoising/smoothing algorithms that I used to remove noise from my data. For those equations unsuitable for parametric management, three non-parametric estimation procedures - Spline, Smoothing Spline and Local Regression - are offered.File Distribution Notice of TableCurve 2D Shareware -TableCurve 2D Free Download -2000 Shareware periodically updates software information of TableCurve 2D from the publisher, so some information may be slightly out-of-date. Tablecurve 2d free download. A non-parametric procedure and the Elgende composition denoising feature, where separation is based on the signal strength, is also available. You should confirm all information before relying on it.
CLICK HERE TO DOWNLOAD Greenox Exploit Scanne
CLICK HERE TO DOWNLOAD 8500 SQL Dorks